In a scenario where you want your website to be publicly accessible by all users, in that case, you cannot apply IP restriction to your website. Such Azure App Services (Web Apps) are publicly exposed to the Internet by default, accessible with their custom domain or *.azurewebsites.net URL, making it vulnerable to hackers and spammers, including Distributed Denial of Service (DDoS) attacks.
An Application Gateway Web Application Firewall (WAF) tier (prevent mode) can help protect against Layer 7 (HTTP/HTTPS/WebSocket) attacks. Application Gateway is an HTTP load balancer that allows you to manage traffic to your web apps. As it operates at layer 7 (application layer), it can scan incoming requests using OWASP common vulnerabilities rule set.
Many a time, it has observed that users face difficulty in configuring their apps services with Application Gateway, especially in a multi-site scenario or app services having multiple custom domains.
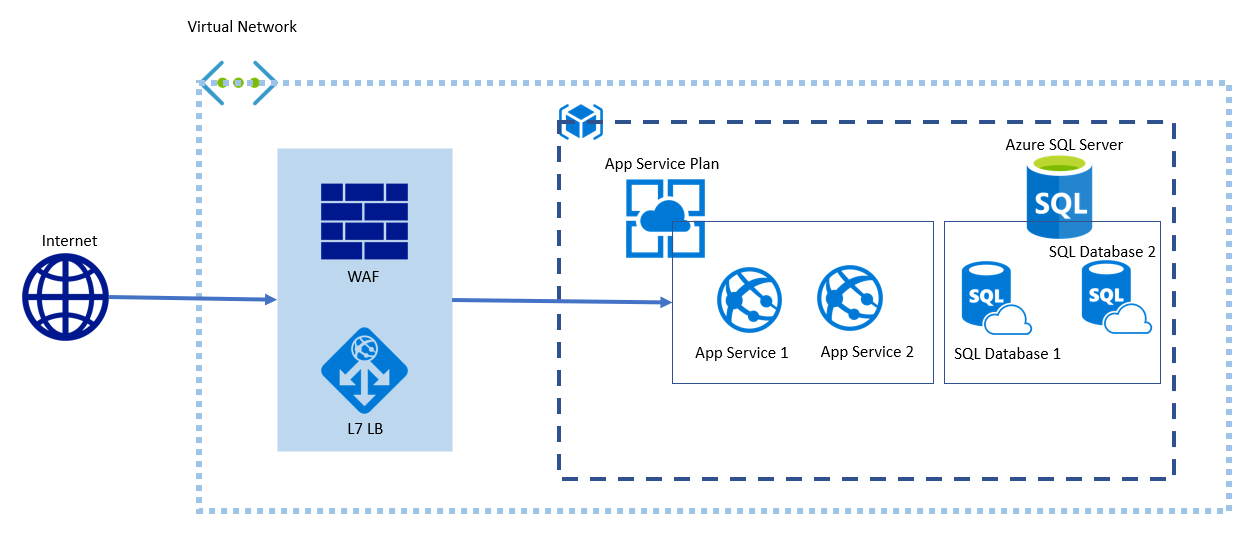
How to configure application gateway with Azure app service
In this article, I ‘will be providing some key points to consider when configuring the Application Gateway with Azure App Service multi-site scenario.
App Gateway Configuration
To prohibit the application gateway to reach your app service, ensure that Network Security Group (NSG) is not applied or blocking your Firewall Subnet.
Backend Pool Configuration
Ensure that you associate your app service in the target. To do so, select “App Services” as Target Type and choose your app service name from the Target bar drop-down.
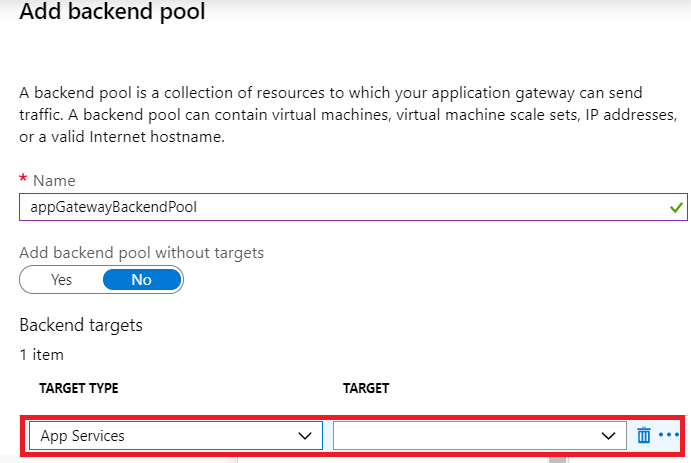
Note: If you have multiple custom domains in a single app service, one app service as a backend pool will suffice your need. In case you have multiple app services, each with a custom domain, then you need to associate each of your app services by choosing them from the Target drop-down.
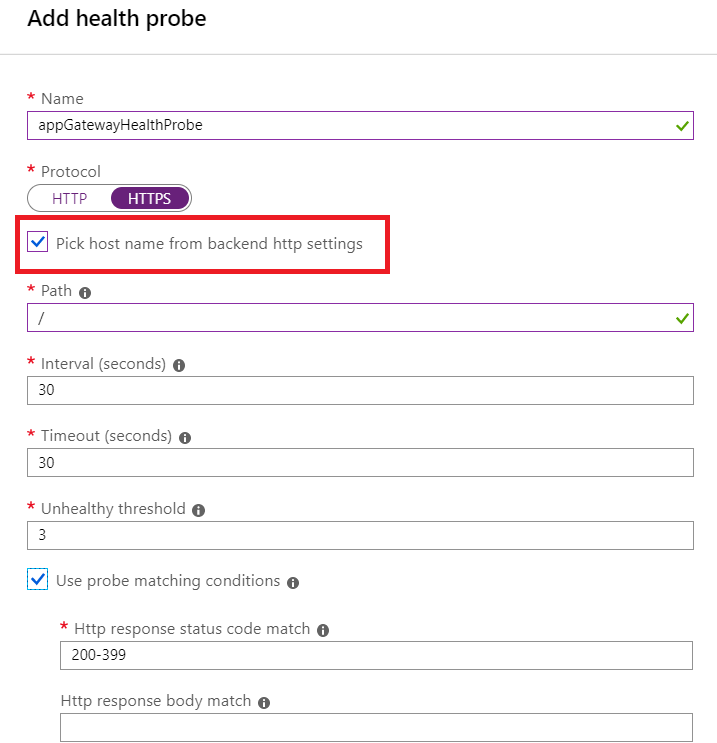
Configuring Custom Probe
You can create a common health probe for all the websites by ensuring that you have checked the “Pick Hostname from backend HTTP settings” so that the probe is picking from “HTTP settings,” which further picks the hostname defined in the app service. That is how it identifies the custom domain rather than just the app service name. You may optionally use matching probe conditions with 200-399 HTTP status response code.
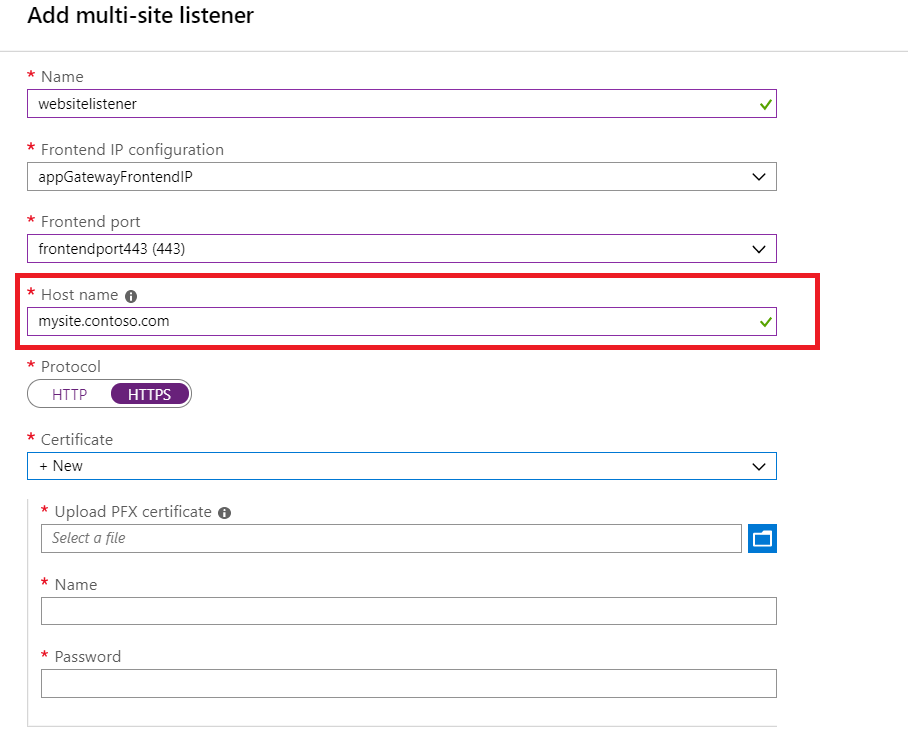
Configuring Listener
When creating a listener, create a multi-site listener. Ensure that you provide your custom domain of the app service in the Hostname field. Choose HTTP or HTTPS based on your website requirement. If your website requires HTTPS, then a PFX certificate for the website is required.
HTTP settings configuration
Create an HTTP setting. Then associate the custom probe and save the HTTP settings again. Make sure that “Use for App Service” is unchecked

Note: You will need to upload .CER certificate if your website requires HTTPS.
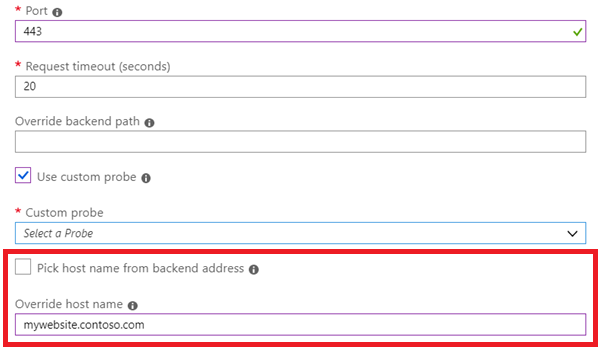
Next, ensure that you keep the “Pick hostname from backend address” box unchecked and provide the hostname of the website in the “Override hostname” field. This action is required when you have multiple custom domains on your website so that Application Gateway understands which custom domain it must pick.
Note: The Request Timeout should be greater than the app service request time. This will allow enough time for the app service to respond before the request times out in the Application Gateway and will help prevent in 502 Server error.
Configuring rule
You can create a basic rule and then associate the Listener, Backend pool, and HTTP setting to it.
Configure redirection (required in case of HTTPS)
After you have created all the above settings, you will need to configure internal redirection if your website is accessible on HTTPS. For e.g., http://mywebsite.contoso.com will not be redirected automatically to https://mywebsite.contoso.com. To do so, you will need to create two things:
1.Create another multi-site listener on port 80.
2.Create another rule and associate it with the listener on port 80.
DNS configuration
To authenticate your app service, you must first add a CNAME record pointing to the app service URL. Example: mysite.azurewebsites.net
Then bind your website with an SSL certificate.
After you have configured the Application Gateway, Listeners, HTTP settings, and health probe look for the Backend Health status. It should be green.
Then replace the CNAME record pointing to Application Gateway DNS instead of the app service. You can find the Application Gateway DNS URL from the Overview section in “Frontend Public IP Address.”
Note: If there are multiple custom domains/websites, the configuration steps mentioned above need to be followed for each website/domain.
Get the cloud services required to develop, manage, and deploy applications on a vast global network with the Microsoft Azure cloud computing platform
Advaiya provide end-to-end services on AWS for cloud solutions. In case of any query, get in touch with our Azure experts or add your comments below.



